-
You just received a friend request on Facebook from someone who’s already a friend
One in a series of posts on Facebook Security and Privacy
First off, don’t panic! Almost certainly your friend has not “been hacked”. Instead an annoying person has just created a new Facebook account and copied your friend’s profile picture and name, and is presumably now going through their friend list asking to become friends.
What can you do?
Use the Facebook “Report” function to let your friend know.
- Open the fake profile page (Just click on the name. Don’t click on Confirm Request!)
- Click on the ‘…’ button (to the right of the Message button), then click Report.
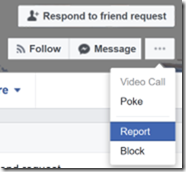
- Select Report this profile and click Continue
- Select They’re pretending to be me or someone I know and click Continue
- Select Someone I know and click Continue
- Select Message your friend
- Type in your friend’s name. Your friend’s existing Facebook profile should be listed.
- Click Send.
- You friend will receive a Facebook message with a link to the offending profile and they can follow it up by reporting it to Facebook.
If you’re particularly concerned, at step 6 you can also choose Submit to Facebook for Review. You will then be asked to select your friend’s real Facebook profile and send it off to Facebook.
-
Facebook security and privacy
I’ve had a number of friends on Facebook suffer the annoyance of having ‘fake’ accounts using the same name and profile picture to impersonate them and contacting all their friends asking to be friends.
It’s frustrating and annoying for everyone concerned. The victim who is being impersonated often also wonders if their Facebook account “has been hacked!”. Usually this is not the case, but I thought it would be helpful to write down some suggestions to help reduce the risk and help you feel more safe using Facebook.
Topics in this series:
- Setting your Facebook privacy and sharing
- Securing your Facebook account with Two Factor authentication
- You just received a friend request on Facebook from someone who’s already a friend
- You just found out someone is impersonating you with a fake account on Facebook
Let me know in the comments if there’s anything else I should cover.
-
MVP Community Connection 2017
 Friday morning I took the day off of work so I could fly over to Sydney to take part in a gathering of Australian Microsoft MVPs. Friday afternoon there was a networking/”unconference” event held at Microsoft’s North Ryde campus.
Friday morning I took the day off of work so I could fly over to Sydney to take part in a gathering of Australian Microsoft MVPs. Friday afternoon there was a networking/”unconference” event held at Microsoft’s North Ryde campus.Later we travelled back to Darling Harbor to have some fun at Strike, trying out their Escape Rooms (lots of fun).
The next morning we gathered for breakfast followed by a full day of speakers and workshops. Everyone got these really nice cards of appreciation with personalised Lego mini-figures. Not sure that my hair is brown, but then I’m not really sure what colour it is – the days of being blonde, or even ‘dirty’ blonde are well behind me 😀
During the afternoon, I was asked to do a short presentation about running a user group. I can tell you I was more than a little bit nervous getting up in front of such an experienced group of people, but I think it went ok.
Early Sunday morning, I flew back home. All in all a great time catching up with friends and learning a lot.


